https://learn.microsoft.com/en-us/intune/intune-service/enrollment/macos-laps
Introduction
Managing macOS devices with Intune is a breeze when you’ve got the right settings in place - so much so that your users don’t even need to be admins anymore. I know, convincing macOS users they don’t have admin rights can feel like convincing a cat to take a bath. But with features like Platform Single Sign-On (SSO) and integration of your Macs in Apple Business Manager for Automated Device Enrollment, you can ensure security while seamlessly managing all application settings and permissions on the device. The possibilities are endless.
However, even when users aren't admins, one key element is still missing from Intune: native Local Administrator Password Solution (LAPS) support for macOS. It’s crucial to rotate local administrator passwords regularly to ensure your systems remain secure. In this post, I’ll show you how to use macOSLAPS, a solution developed by Joshua D. Miller, to fill the gap and rotate local administrator passwords on macOS devices.
macOSLAPS Installation and Configuration
To install macOSLAPS, you can use the shell script available on Joshua D. Miller's GitHub page, which will install the latest stable version of macOSLAPS.
The script not only installs the tool but also creates the LAPS admin if a PLIST file with the necessary settings is deployed to the device. We will cover how to configure and deploy this PLIST in the following section. If you’d like, you can modify certain variables in the script, such as the following:
- managedAdminAccountName
- managedAdminAccountPassword
- managedAdminAccountDeleteExisting
- convertLoggedInUserToStandard
I would recommend not changing the other variables.
After setting the variables, deploy the shell script to your test devices in Intune. If you choose to deploy it widely after testing, I recommend assigning the script to all devices using filters, if possible. Don’t use dynamic security groups for any macOS-related policies and scripts, as they are very slow to process.
Creating a PLIST file
Next, you need to create a PLIST file with the LAPS configuration. You can find an example of the file on GitHub.
You can also find all available configuration keys here.
Don't forget the Method configuration key. Since I don't have AD, I use local. Here is my example configuration:
<key>DaysTillExpiration</key>
<integer>30</integer>
<key>LocalAdminAccount</key>
<string>lapsadmin</string>
<key>Method</key>
<string>Local</string>
<key>PasswordLength</key>
<integer>14</integer>
<key>RemovePassChars</key>
<string>{}[]|^'"~`,</string>Deploying the Preference Policy in Intune
Once you've created and saved your .plist file, use the steps below to deploy it to your devices. This policy will create the file edu.psu.macoslaps.plist in the following location:
/Library/Managed Preferences
If the file does not exist, the install script will not perform any actions.
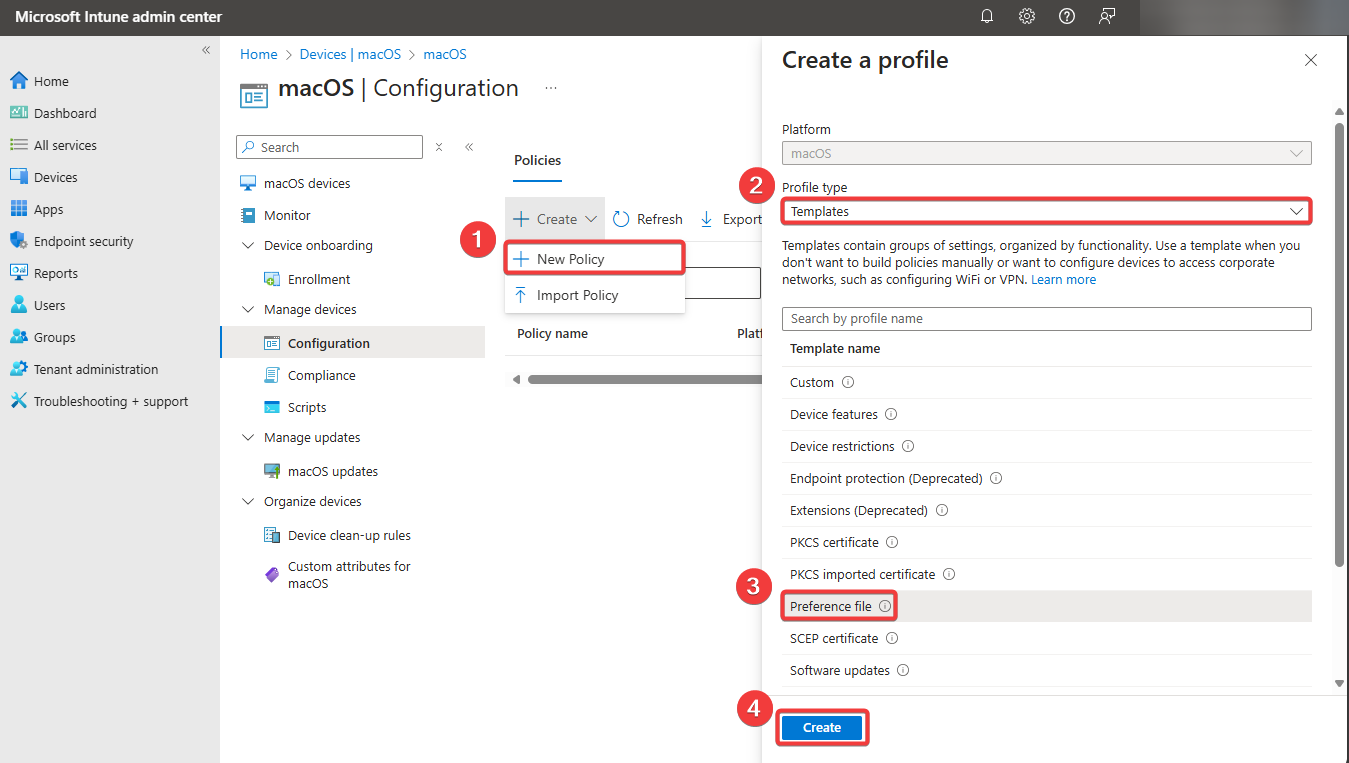
Give the policy a name and upload the PLIST file.
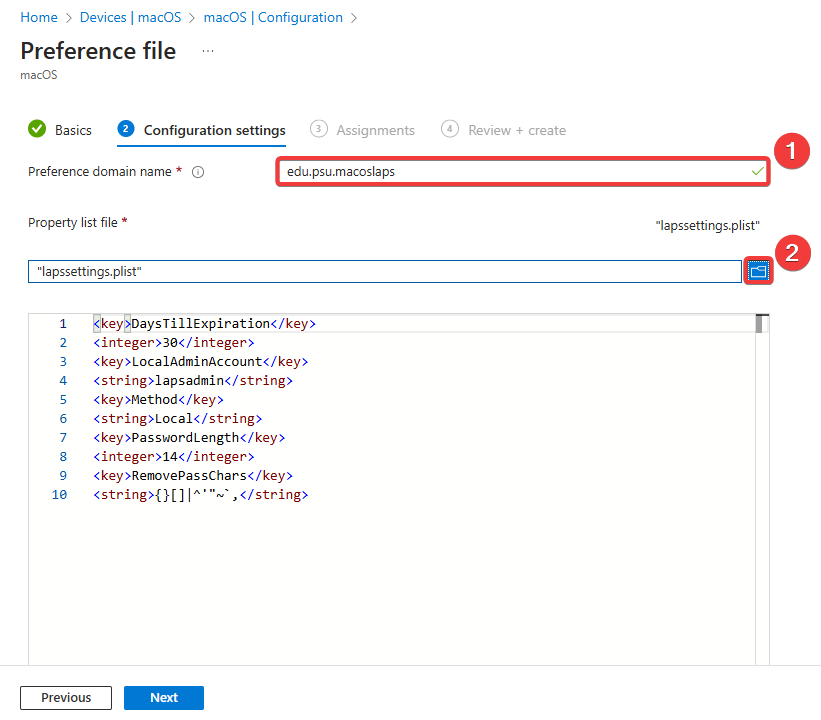
The Preference domain is edu.psu.macoslaps
Assign the policy to your test devices.
Uploading the script for Custom attributes
Custom attributes for macOS in Intune allow administrators to collect and store specific data from devices. For example, scripts can fetch hardware details or last reboot time and store them as custom attributes. We will use this feature to retrieve the LAPS admin password. You can find the script on GitHub.
Edit the rotateTresholdDays variable if needed and upload the script in the Custom Attributes blade in Intune.

Assign the script to your test devices.
After the next device check-in, you should be able to see the password along with the expiration date in Intune:
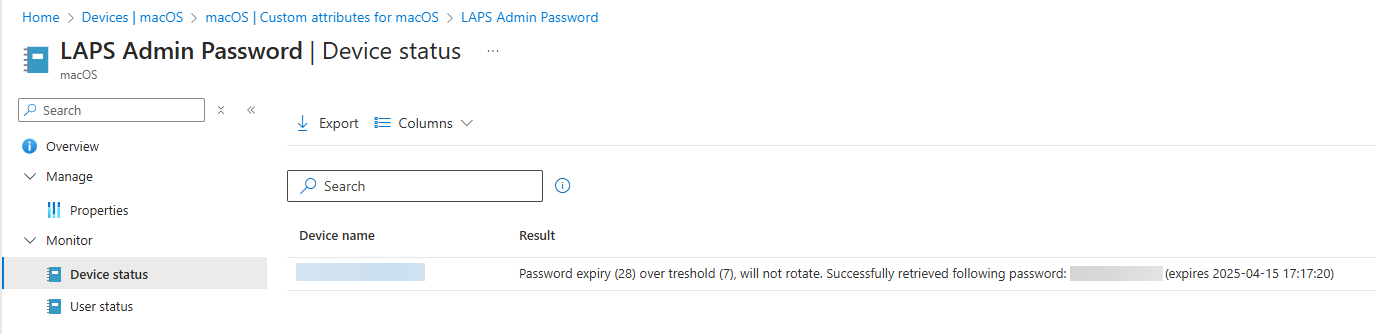
That's it! 🚀
Conclusion
By following the steps outlined in this post, you can install, configure, and deploy macOSLAPS, as well as automate the management of local admin passwords across your devices. The combination of Intune, macOSLAPS and careful policy deployment provides a seamless solution to streamline macOS management.
While Microsoft is expected to release native LAPS support for macOS by the end of the year, macOSLAPS offers a great workaround in the meantime, so you don’t have to wait to secure your macOS devices.
Happy managing!






Member discussion